Digital assets such as Bitcoin and Ethereum are a major asset class, representing over $2 trillion in market capitalization, and are attractive propositions for investors to store and transfer value, with 90% of institutions seeing crypto trading as an opportunity. However, 95% of investors believe fraud in the crypto world is "somewhat or very much prevalent”.
Ever since early humans started experimenting with setting things on fire, new technologies have offered great promise but also brought with them new risks. In this emerging new market, how do investors protect their investments and avoid getting burned?
Some important scene-setting
Before we talk about the fraud and theft risks and how these might be mitigated, it’s probably worth quickly discussing a few fundamentals of these new types of assets.
From a crypto perspective, a ‘digital asset’ is a digital representation of something – a token or picture – that can be transacted on a blockchain. Digital assets can be transferred using emerging technology that obviates the need for a central party (i.e., bank or intermediary), where records of ownership are stored on a type of distributed ledger (usually publicly available) known as a blockchain. Transactions are near-instant and final – bringing the advantages of trading speed and low cost, but the potential disadvantage of non-reversible transactions.
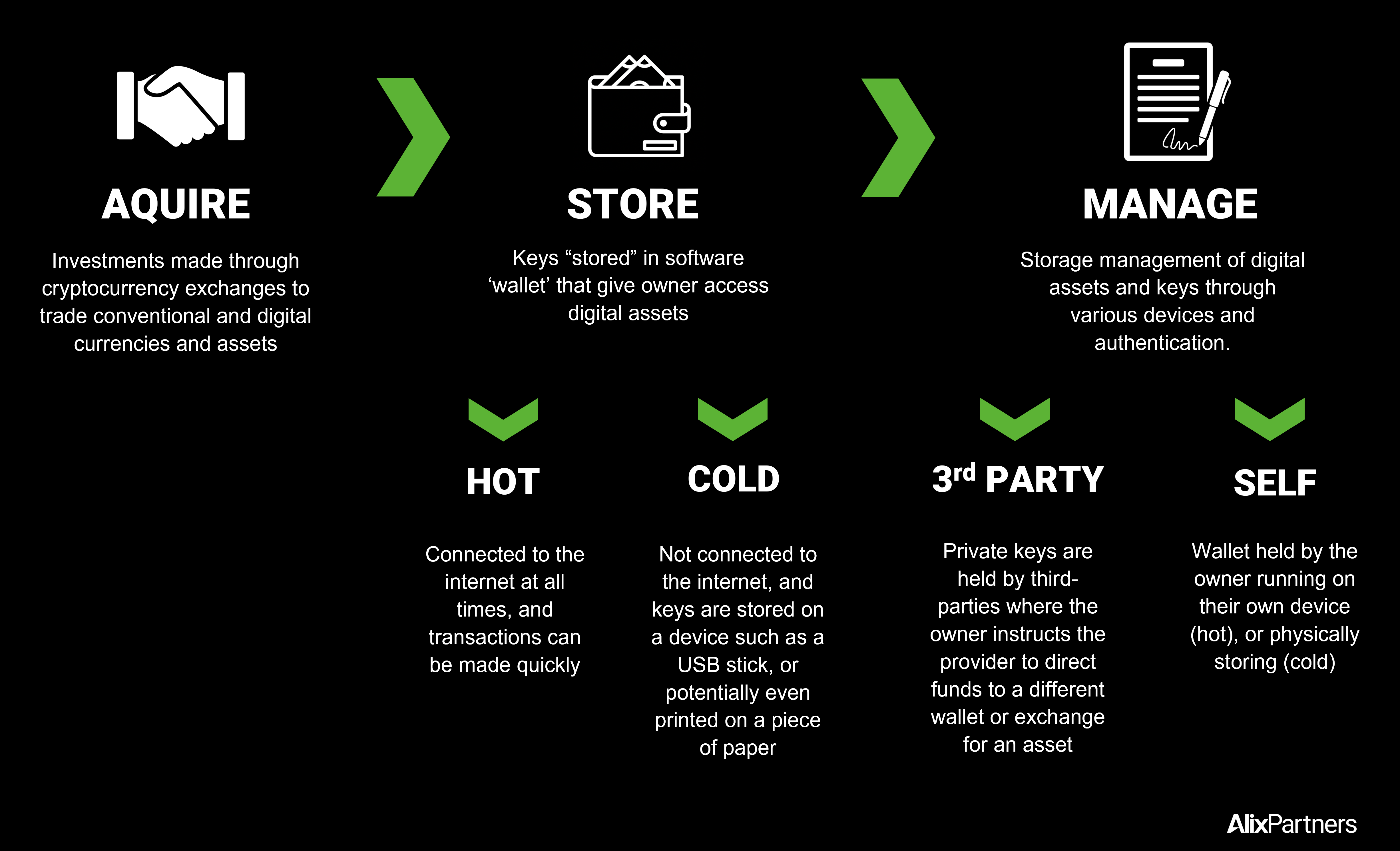
The digital asset ecosystem is made up of several components, allowing investors to acquire, store and manage, and trade assets. Beyond mining, the ecosystem is made up of the following components:
- Acquire - Investments are typically made through cryptocurrency exchanges such as Coinbase, allowing trades of conventional and digital currencies and assets.
- Store – Digital assets are typically “stored” in software programs called ‘wallets’. However, wallets don’t technically store assets. It’s easiest to think of a wallet as a keyring, as they hold the keys (in particular the so-called “private key”) that allow the owner to access their digital assets, and which are required to securely complete a transaction. Wallets can be categorized as:
- Hot wallets, which are connected to the internet at all times, and transactions can be made quickly.
- Cold wallets, which are not connected to the internet and keys are stored on an external device such as a USB stick, or potentially even printed on a piece of paper.
- Hot wallets, which are connected to the internet at all times, and transactions can be made quickly.
- Manage – There are two-main types of storage management: third-party digital asset custody and self-custody.
- Third-party custody is when private keys are held by third-parties. This is most common where you have a wallet that is hosted by a centralized exchange, which is accessed via similar authentication methods as used to access your bank account. The exchange holds the keys, but you can instruct the provider to direct funds to a different wallet or exchange for a different asset.
- Self-custody is when the wallet is held by the owner. This could be a hot wallet that the owner runs on their own device, or a cold wallet that they’re physically storing.
- Third-party custody is when private keys are held by third-parties. This is most common where you have a wallet that is hosted by a centralized exchange, which is accessed via similar authentication methods as used to access your bank account. The exchange holds the keys, but you can instruct the provider to direct funds to a different wallet or exchange for a different asset.
One key takeaway is that, for most crypto-assets, control (and de-facto ownership) of that asset is associated with knowing, or having access to, the private key to unlock those funds. If another individual was to gain access to that key, then those funds effectively belong to them too, and can be transferred to an account that only they can access. This is why we have the expression “Not your key, not your coin”.
So, how might that happen?
Mugging the user
The most direct way for an individual to get their hands on your crypto holdings is to either get hold of your private key directly, or, if the keys are in the custody of an exchange, convince the exchange to hand them over. There are multiple methods of achieving this goal, and we’ll discuss a few of the most common ones below:
Phishing
Phishing has been around for decades and consists of a hacker sending targeted messages, to a particular user or group of users, with the aim of having the user voluntarily give up information that allows the hacker access to sensitive information such as a password or private key.
This is arguably the easiest for a user to protect themselves against, as it relies on good cybersecurity hygiene which should be practiced regardless of the use of crypto-assets. However, the relatively new and unfamiliar world of cryptocurrencies will arguably make it easier for a hacker to reel in a catch.
Social Engineering
Cryptocurrency exchanges, much like banks, often have similar security features allowing users to reset their passwords or otherwise gain access to their accounts in the absence of a password. This can often rely on the user being asked to provide information known only to the user, such as a memorable address, name, or date. Hackers can use information that users either voluntarily share with the world (e.g. via social media), or attempt to gain this information from the user directly under false pretenses. They are then left with the task of convincing a human at an exchange that they are the genuine owner of the account, leaving the fate of the asset at the behest of human fallibility.
As with phishing, prevention here centers on good information security hygiene, such as keeping social media profiles private and not sharing information that may be used as a security question. These messages should be a feature of any good security awareness training program.
SIM swapping
Many organizations use SMS messages as a form of two-factor authentication, where a one-time login code is sent via SMS to a user‘s mobile phone when attempting to access their account. They may also form a part of a password-reset process. However, it is possible for hackers to hijack these text messages by effectively stealing your mobile phone number by having it reassigned to a new SIM. This can be as simple as entering a mobile provider’s store and convincing an unwitting employee (or bribing a corruptible one) that you’ve lost your SIM and wish to get a new one issued.
Many security professionals don’t consider SMS messages to be a good form of two-factor authentication. Where possible, users should use (and find wallet providers that offer) other authentication methods, such as authenticator apps or hardware authenticators, and avoid SMS messages entirely for this purpose.
Malware
Finally, hackers might attempt to infiltrate your device using malware. This can be in the form of e-mails with suspicious attachments, users installing untrustworthy software, or even installing fake browser extensions. Once hackers have software installed there are multiple ways you might lose your assets:
- Key loggers may be used to collect credentials for wallet providers.
- Keys from wallets held on the user’s devices may be directly stolen.
- So-called clipboard-hijacking malware can replace a wallet address in the clipboard with a different address, effectively tricking a user (who is likely copy-pasting the wallet address of an intended recipient) into willingly transferring funds to a hacker.
Robbing the bank
If an attack against a user is like a mugging or a house robbery, then an attack against a cryptocurrency exchange, which will host wallets for millions of users, is more akin to robbing a bank. Cryptocurrency exchanges can control billions of dollars’ worth of assets, so represent very rich targets for hackers.
Cryptocurrency exchange hacks are almost as old as cryptocurrency exchanges themselves, with the Mt Gox hack being the first major hack, and still a name almost synonymous with crypto exchange hacks. Hackers may aim to gain the credentials of users of the exchange, which they can then use to access accounts and steal funds. Or they may even gain the private keys from the wallets hosted and controlled by the exchanges (which are typically internet-connected “hot wallets”) and then empty the funds into their own wallets, in a metaphorical equivalent to emptying the bank’s vault.
Exchanges are, of course, staffed by humans, so some of the vectors for an attack against exchanges have some similarities. For example:
- Malware – Hackers will try to place malware on devices within the corporate network, giving them access to the software and systems that operate the exchange.
- Phishing – Hackers might also try to gain employee credentials, allowing them to access systems whilst masquerading as an employee of the exchange.
However, in addition, exchanges operate as public services. It’s not possible for an exchange to wall itself off from hackers by not allowing any outside connections, and they must maintain a way for its users to interact with them (e.g. apps, websites). Consequently, any possible vulnerabilities in the software that exchanges are using, of which there can be many, all provide potential routes for hackers to gain ingress into the system and gain user credentials or the user’s private keys themselves. These kinds of breaches have a well-documented history of taking place across a multitude of public-facing websites, and exchanges have the added burden that such a breach places their customers at risk of direct financial loss.
As users or investors, there’s little we can do directly to protect ourselves from an exchange being hacked. Some due-diligence and risk mitigation methods include:
- Using well-established exchanges with a track record. Newer exchanges, particularly those offering low fees, may have less mature cybersecurity functions and be more vulnerable to hacks.
- Spreading funds across multiple exchanges.
- Understanding the insurance terms and conditions of exchanges, particularly any limits on coverage (e.g. for traditional banks, the FSCS compensation scheme has an upper limit of £85,000).
- Using a separate “cold wallet” where funds are stored outside of an exchange.
So where does this leave us, as investors?
Digital assets present an exciting new opportunity for investors. However, much like any investment, investors must do their homework before making a decision and ensure the relevant safeguards are applied to ensure themselves, the transacting company, and their investments are protected. In summary:
- Practice good information hygiene and follow cyber-security best practices.
- Caveat emptor – complete due diligence on the exchanges with which you wish to do business.
- Risk mitigation can be improved by maintaining funds with different exchanges or in offline “cold wallets” that are harder to hack.
In the next part of this series, we will further focus on smart contracts and distributed finance, and the risks associated with that emerging market. We will also consider how the explosive growth in the sector - and the appeal of the high returns that some investors have achieved so far - have also attracted a number of more traditional scams and frauds.


